The NYT has a shocking story about a man who accidentally “hacked” his way into someone else’s American Express account. Allan Goldstein, an honest man, immediately called American Express’s customer support to notify them of the accidental breach. He got a rep in India, and then several others who had no clue what the issue was. It took more than twenty days later, six different American Express customer service reps, and a call from a New York Times writer for American Express to get on the ball.
This is the AmEx flack’s explanation:
Ms. Alfonso confirmed Mr. Goldstein’s story for me. She called the problem “an unusual case of two customers coincidentally having nearly identical log-in information, which led one card member to inadvertently log in to another card member’s account.â€
Nearly identical log-in information? So perhaps Goldstein and this mystery lady’s account had the same name and the same password? What are the chances of that happening?
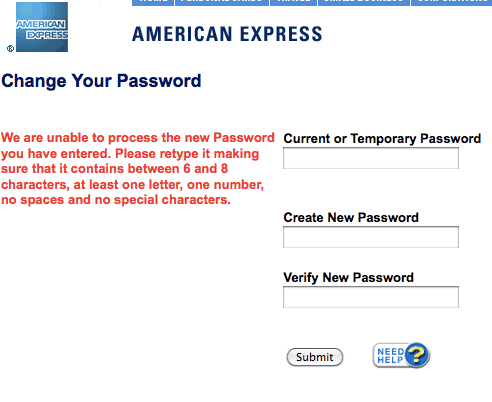
Well, pretty slim, but not out of this world, thanks to American Express’s astonishingly weak password protocols. I started an account with them more than a year ago and was amazed to find out that I could not create a password greater than 8 characters. I just checked, and it’s no different today:
Not only is it eight characters, but case doesn’t matter, and non-alphanumeric characters don’t work:
Your Password should:
* Contain 6 to 8 characters – at least one letter and one number (not case sensitive)
* Contain no spaces or special characters (e.g., &, >, *, $, @)
* Be different from your User ID and your last Password
Is there any other major online service today that has such a primitive, limited space for passwords? Eight alphanumeric characters was considered good enough back in the 1970s. Think about it; even your MySpace account has stronger security than your $10,000-limit credit card (ok, don’t know that for sure…it’s been awhile since I had a MySpace account).
Coincidentally, this week the NYT had a story about weak passwords, from a security analysis of the 32 million passwords stolen from the idiots at RockYou:
In the idealized world championed by security specialists, people would have different passwords for every Web site they visit and store them in their head or, if absolutely necessary, on a piece of paper.
But bowing to the reality of our overcrowded brains, the experts suggest that everyone choose at least two different passwords — a complex one for Web sites were security is vital, such as banks and e-mail, and a simpler one for places where the stakes are lower, such as social networking and entertainment sites.
Mr. Moss relies on passwords at least 12 characters long, figuring that those make him a more difficult target than the millions of people who choose five- and six-character passwords.
The problem with an eight-character alphanumeric password limit is that not only is there a limited choice of passwords, but you have less room to make easy-to-remember-but-secure passwords. For example, I’ve used phrases from favorite stories and songs. Something like: “itwastheBestOfTim3$” (this is not particularly secure, since it’s a composition of dictionary words, but you get the idea). So even though there is room for hundreds of billions of password combo…that space is only helpful if human beings can be relied on to generate random strings for passwords. The above NYT article suggests they can’t…so Joe Average, instead of being able to make up something like Password123456!, is limited by AmEx to Passwrd1. Neither is a very strong password, but there’s a chance for many more coincidental collisions in the latter case.
The terrible customer service that Mr. Goldstein experienced is galling…but the root of the problem, assuming the flack’s explanation is correct, is AmEx’s antiquated password-storage system. I hope they don’t keep it in plaintext, as the security-lax folks at RockYou did.
Snowulf wrote about this back in 2007.